In this sample chapter from macOS Support Essentials 10.15 - Apple Pro Training Series: Supporting and Troubleshooting macOS Catalina, authors Karneboge and Dreyer describe when the command-line interface is useful, use man (manual) pages to find more information about commands, and manipulate files in the command-line interface.
Use the command-line interface (CLI) to access additional administrative functionality.
Reference 4.1 CLI Basics
The CLI includes these advantages:
Additional administrative and troubleshooting options are available from the CLI. For example, the following apps have CLI equivalents that include additional options: System Information (system_profiler), Installer (installer), Software Update (softwareupdate), Disk Utility (diskutil), and Spotlight (mdfind). These are just a few instances, as nearly every administrative function has both a graphical and a command-line tool.
From the CLI you have more access to the file system. For example, the Finder hides many files and folders that are visible in the CLI. Also, there are many file-system permissions settings that the Finder doesn’t display.
You can remotely log in to a Mac computer’s CLI using the Secure Shell (SSH) protocol. The next section contains more information about SSH.
By using the sudo command, any administrator can run commands as the System Administrator user, also known as root. This enables greater administrative flexibility in the CLI. Read Reference 7.1, “User Accounts,” for more information about the root account.
If you are comfortable with the CLI syntax, you can apply it to a command-line script. This enables you to automate repetitive tasks.
If you combine CLI instructions with Apple Remote Desktop (ARD), you can remotely administer multiple, even thousands, of Mac computers simultaneously. ARD enables you to remotely send the same command to several Mac computers with one click. For more information about Apple Remote Desktop, go to www.apple.com/remotedesktop.
Access the CLI
A shell is the first command that runs when you access the CLI. It displays the CLI. You can access the CLI in several ways:
You can use Terminal. It’s in /Applications/Utilities/Terminal. Terminal has a customizable interface. It includes a tabbed interface for multiple command-line sessions, multiple split panes for viewing history, support for full-screen mode, and Touch Bar shortcuts.
Use macOS Recovery to open Terminal from the Utilities menu. Or for a Mac that does not have the Apple T2 Security Chip, at startup press and hold Command-S to start in single-user mode. Single-user mode is also available for a Mac with the T2 chip if you configure the Secure Boot setting to No Security. This mode starts the minimum system required to provide you with a command-line prompt so that you can enter commands to troubleshoot a Mac that can’t fully start up. Read more about single-user mode in Lesson 28, “Troubleshoot Startup and System Issues.”
SSH remote login enables you to securely log in from a remote computer to access your Mac computer’s command line. SSH is a common standard, so you can use any operating system that supports SSH to remotely log in to your Mac. This remote access allows administrators to make changes at the command line without alerting the user to their work. Before you can use SSH to connect to your Mac, you have to turn on SSH access.
Work in the Command Line
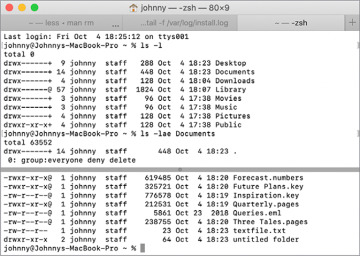
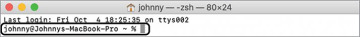
When you first open Terminal, it may display information about your last login. Then it will display the prompt.
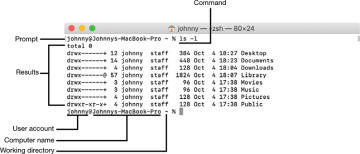
The prompt indicates that you can enter a command. By default, the prompt shows you the following:
Your current user account name
The @ symbol
The name of the Mac you’re using
Your location in the file system
A special character that provides a hint about which shell you’re using
macOS Catalina uses the Z shell (zsh) by default, but if you upgraded your Mac from a previous version to macOS Catalina, you might still be using the bash shell:
zsh uses % at the end of the prompt.
bash uses $ at the end of the prompt.
Read Apple Support article HT208050, “Use zsh as the default shell on your Mac,” for more information about different shells, including instructions about script compatibility.
Where you are in the computer’s file system is called the working directory, and it changes as you navigate through the file system.
At the prompt, you enter your command string, often more than one word, and press Return to initiate or execute the command.
An executing command takes over the Terminal window with a text interface, shows the results of the command, and returns to the prompt, or performs some work and returns to the prompt when complete. Many commands display results only if a problem occurs. Read what the command returns to make sure it doesn’t indicate a problem.
Some commands take time to execute and may not give a progress indication. If a new prompt does not appear, generally assume your last command is still running.
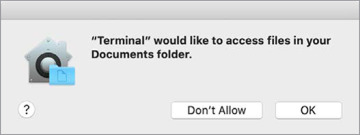
When you use Terminal to access portions of your home folder for the first time, macOS asks for your explicit approval. You’ll see the results of your privacy decisions in the Privacy pane of the Security & Privacy preferences in System Preferences. Read Reference 9.5, “Manage User Privacy,” for more information.
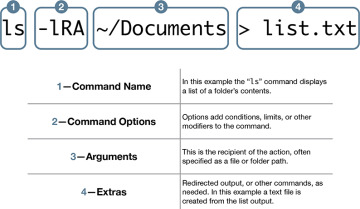
Command String
The command string includes a few parts:
Command name (1)—Some commands just need you to enter their name to execute.
Command options (2)—After a command name, you might specify options (or flags) that change a command’s default behavior. Options might not be required and can be different for every command. Options start with one or two dashes to distinguish them from arguments. Many commands can include several single-letter options after a single dash. For example, ls -lA is the same as ls -l -A.
Arguments (3)—After the command and its options, you typically specify an argument (or parameter), which is the item or items you want the command to modify. An argument is needed only if the command requires an item to act upon.
Extras (4)—Extras aren’t necessary, but they can enhance the capabilities of a command. For example, you could add items that redirect the command output, include other commands, or generate a document.
Command-Line Example
Here is an example in which the user Joan works on a Mac called MyMac and her working directory is her Documents folder. She deletes a file called Junk.txt. Joan presses Return after she enters her command.
joan@MyMac Documents % rm Junk.txt joan@MyMac Documents %
In this example the command was entered and executed properly, and macOS returns to a new prompt. This is an example of a command that returns information only if it didn’t execute properly. The Mac usually lets you know if you entered something incorrectly by returning an error message or help text. macOS won’t prevent or warn you from entering a destructive command, such as accidentally deleting your home folder. Always double-check your typing.
Use Manual (man) Pages
When you want to learn more about a command, you enter man followed by the name of the command. Manual (man) pages include detailed information about commands and references to other commands. After you open a man page, use navigation shortcuts to move through it:
Use the Up Arrow and Down Arrow keys to scroll.
Use the Space bar to move down one screen at a time.
Enter a slash (/), enter a keyword, then press Return to search through a man page.
Exit the man page by typing q.